The fraudsters could use the credentials of high-profile employees to gain access to sensitive company information such as intellectual property or trade secrets.
Are You Doing Enough to Prevent Account Take Over in your Company
I am sure your business is taking preventative measures but you have to ask yourself is it enough? Yes, you have strongly advised all account owners to use strong and unique passwords, you have even recommended password managers they could use. You have also ensured that they are using multifactor authentication. But, is it enough? The answer is no. Truth is that there is no amount of security provisions that can guarantee full protection. Because hackers are always coming up with new ways to infiltrate your system. However, you can take all the necessary measures so that if you ever get compromised then it’s not because of something you could have avoided.
Using SolarWinds Identity Monitor to Prevent ATO
So, on top of all the security measures you already have installed, I am going to recommend another solution which is also, arguably, the most effective in stopping account takeovers. A tool that scans the internet for exposed data and notifies you if any of the data is related to your business. The SolarWinds Identity Monitor. I have to admit when SolarWinds announced the launch of this solution, I was genuinely excited. Not because similar solutions did not exist before but because of the respect I have for the company. I am yet to come across a SolarWinds product that was a disappointment. The SolarWinds Network Performance Monitor is considered to be the best when it comes to troubleshooting and fixing network problems. But enough of that. Let’s focus on the topic at hand. SolarWinds Identity Monitor. Why should you use it?
Why you should trust SolarWinds Identity Monitor
Sure, coming from a reputable company does give the product some credibility but I am sure you are looking for something more tangible. And I will get into that when discussing the product’s features but how is this for a start.
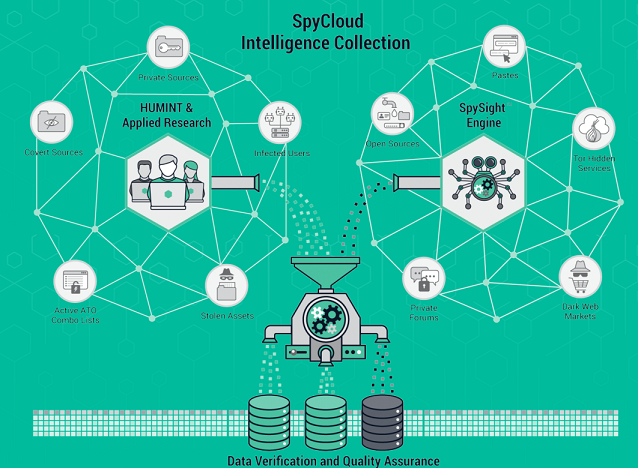
SolarWinds Identity Monitor is a Collaborative Effort Between SolarWinds and Spycloud
Spycloud is a big data company known for its effective dark web monitoring solution and an expansive database of breached information. The essence of SolarWinds Identity Monitor is to identify when login credentials associated with your company are exposed on the web and what’s more reassuring than knowing that they run your monitored information against the most current and complete database. Spycloud combines Human intelligence gathering with automated scanning allowing them to access the same data that the ATO fraudsters have. The Spycloud algorithms are far more effective than dark web scanners and can identify breached data weeks or months before the scanners do.
Your information is monitored in real-time
Once you have specified the domain and email addresses that you want to be monitored, they are automatically added to the Identity Monitor watchlist. They will then be continuously run against the database every time it is updated allowing you to get notified immediately your information is involved in a breach.
Uses data from public and non-public sources
Yet another perk of partnering with Spycloud and also the reason why SolarWinds Identity Monitor is better than your average scanner. Most scanners will only access data once it has become public. This gives hackers enough time to use the data acquired from private sources to execute an account take over.
Installation
SolarWinds Identity monitor is a web application and thus needs no installation. Here is how to get started with the tool. On the product’s official website, look for the field requiring you to enter your email address. Fill in the address that you want to be monitored and SolarWinds will mail you a link directing you to the web application. For the purpose of testing, Identity Monitor allows you to monitor one email for free. If you need to monitor a whole domain or additional emails then you will need to subscribe to a premium plan.
SolarWinds Identity Monitor Features Overview
Now that you are in, let’s see what features make this product the best for preventing ATO.
Intuitive Interface
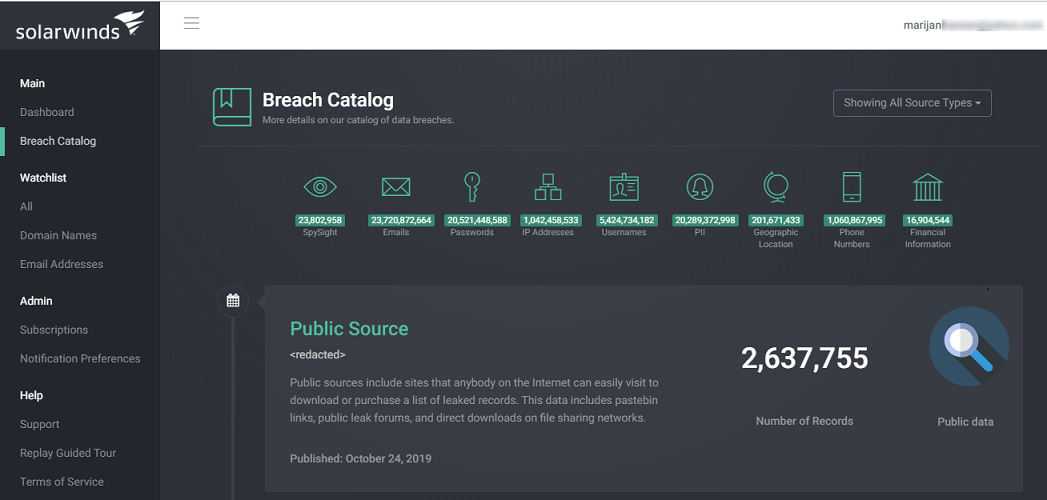
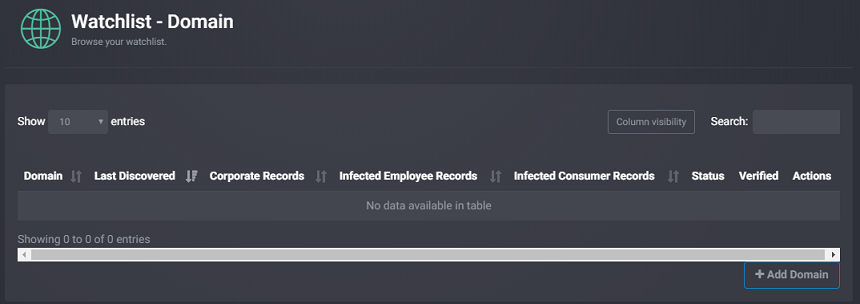
The first thing that caught my attention after logging in to Identity Monitor is how well it has been organized. It is split into 4 main sections that can be accessed from the left pane on the interface. The main section is where you check the status of the data that you are monitoring. You can tell if there has been a breach and the timeline during which it occurred. Identity Monitor will also tell you the type of data that was leaked and the source of the leak.
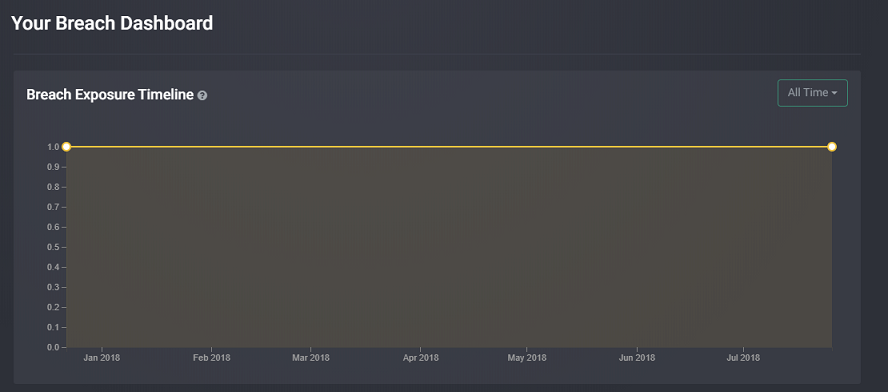
Graphical Representation of your Breach Timeline
Every time there is a data breach incidence involving your monitored data, it is recorded on your breach timeline. And if you are monitoring multiple domains and emails then it can be a little hard keeping track of all the incidences via the chronological listing. Fortunately, Identity Monitor includes a graph with all the breach incidences which is much easier to follow. You can go back in time and check the details of any data breach that exposed your data.
Email Notifications
Good news. You don’t have to log in to the Identity Monitor application every time you want to check where your accounts may be compromised. The tool is always doing checks and will notify you immediately there has been a data breach. This allows you to take prompt action like executing a password reset for all your accounts or having the account owners set up multi-factor authentication. Also, you can add more than one email address. This means that you can include the addresses of all your team members and whoever receives it first can begin the remediation process or notify other parties.
Can Monitor Multiple Domains
There is no limit to the number of domains you can monitor using this tool. It all depends on the subscription plan you purchase. Even better, once you have added a domain, Identity Monitor allows you to monitor all the email addresses associated with the domain. The tool also allows you to monitor private email addresses, The most basic subscription supports only 25 emails so you have to choose only the high-profile individuals with the highest risk factor to monitor their personal emails.
SolarWinds Identity Monitor Pricing
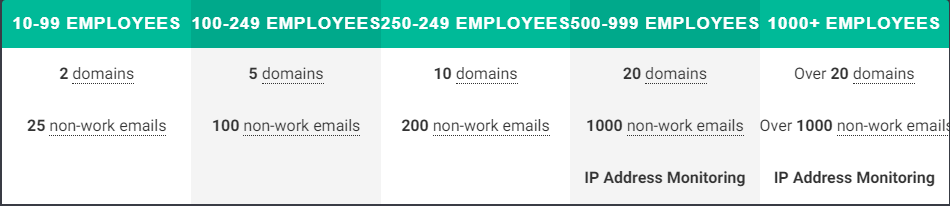
The SolarWinds identity Monitor is available in 5 premium plans. The most basic plan is ideal for businesses with 10-99 employees and can be used to monitor two domains and 25 personal emails. The highest tier plan is tailored for businesses with over 1000 employees and has no limit to the number of domains or non-work emails you can monitor. There is no mention of the actual prices for each plan just that pricing starts at $1795. You can contact SolarWinds to get a quote for your desired plan.
Conclusion
Well, Brandon Shopp, the vice president of product strategy for security, compliance, and tools at SolarWinds has the best summary for this post. So to quote what he said, “Account takeovers are a significant risk to businesses of all shapes and sizes, but there are too few ways to know and respond to these types of threats in a timely manner. With Identity Monitor, everyone from the security pro to the systems administrator can easily mitigate the threat of low-hanging vulnerabilities like employee credential thefts, while at the same time encouraging a more proactive security posture within their organizations.”
How to Track your Domain’s Leaked Credentials using Identity Monitor?SolarWinds Network Performance Monitor (NPM) - A Comprehensive ReviewSOLVED: Safari Can’t Verify the Identity of the Website Error MessageFix: The Identity of This Website or the Integrity of this Connection Cannot be…