Note: There are many variations of this scam, but the method of operation is always the same. The issue is not specific to a certain browser or operating system. Depending on the device that is being used, the same message can be encountered on every Windows and Mac version.
The method of operation
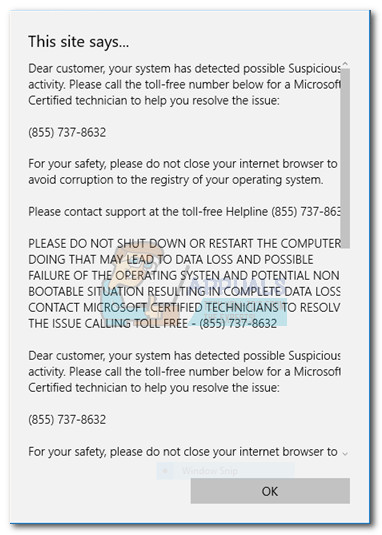
We should start by mentioning that your system is not actually infected unless you call the number and follow the instructions provided in the scam pop-up page. If the user ends up calling the provided assistance number it will often connect to an individual with a heavy foreign accent, parading as a Microsoft or Apple support tech – depending on the platform used by the victim. During this phone conversation, the cybercriminal will usually guide the victim towards giving away remote control of the PC. Once remote access is achieved, the user’s web browser will be hijacked. At this point, restarting the computer in an attempt to remove the pop-up will become effective – typically, the user will be presented with the same scam page whenever the browser is opened. If the user has gotten this far in the scam, most of the damage has already been done. By now, the attacker has full remote access to the victim’s computer and can freely engage in illicit practices. Immediately, one has to assume that every saved password is probably compromised, as well as any bank information. If the victim is still unsuspecting, the cybercriminal might also try to sell some services in order to fix the “corrupted computer”. There are also reports of keyloggers and trojans being planted at this point if the victim is still not aware of the scam.
The technical aspects of it
The vast majority of these pages are driven by an affiliate network and can be linked to malvertising since they often linked with other dubious ads. We have seen joint efforts to shut down these scam sites, but the results have not been satisfactory. There’s a flurry of new scam pages for every page that get’s shut down. Security researchers investigated the alarming rise in scam sites such as these and discovered some interesting results – the vast majority of these sites are so poorly secured that their index is often browsable. Even more, all of them have a code snipped that disables right-clicks and prevent you from closing the browser window. Most (if not all) domains used for this scam are set up through some sort of proxy or anonymous registration. Because there is no honor among thieves, they often steal content and malicious code from each other by deploying various web crawlers.
How to deal with a pop-up scam
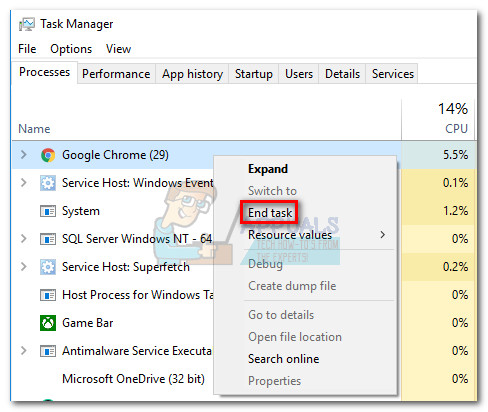
The best possible advice that can be given when dealing with these fake alerts is to remain calm and close them forcibly. Despite being prompted to act urgently, you should never call the toll free number, let alone grant the fake “tech support agent” remote access to your device. Closing the pop-up conventionally will most likely not be possible because of an annoying script that will prevent you from doing so. Instead, users are advised to force close them by whatever means necessary. On Windows, you can do this by opening Task Manager (Ctrl + Shift + Esc), right-clicking on the web browser that’s displaying the pop-up and choosing End process (End Task). Finally, reboot your PC and re-open the web browser.
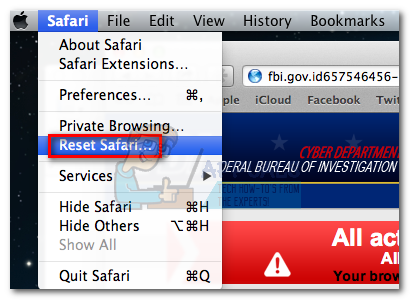
On a Mac, expand the Safari menu from the top ribbon and choose Reset Safari. Then, make sure all items are checked and hit the Reset button. Once the reset is complete, simply re-open the browser again.
After you open up the browser again, do not click the Restore session button, otherwise, the pop-up will resurface again. Note: If you find that you’re frequently redirected to the same scam page after performing the steps above, there’s a high chance that some possibly unwanted programs (PUPs) have found your way on to your system and are redirecting the traffic towards the scam page. To make sure that you remove every PUP or another malitious program that might be redirecting you towards the scam page, it’s highly recommended that you do an anti-malware scan. If you don’t have a security scanner at the ready, use our in-depth guide on using Malwarebytes (here) to remove any malware from your system.
How to stay safe
Given the fact that these types of scams are all too efficient, they are not going away anytime soon. Bad guys have gotten a lot better at using social engineering tactics to entice their victims, so we advise caution and rationalizing before acting out of instinct. As a rule of thumb, every browser pop-up that parades as a Microsoft or Apple prompt and refuses to close should be regarded as a scam. After all, Microsoft and Apple’s answer techs are known for being notoriously unhelpful – it would be absurd to believe they will take it upon themselves to solve your issues before you contact them first.
Fix: Error Code 475 - Suspicious Activity was detected on your accountFix: The System Detected a Possible Attempt to Compromise SecurityHow to Fix No Boot Disk Has Been Detected or the Disk Has FailedHow to Fix “Friend Activity Not Showing” on Spotify?